How Do You Get Hacked ? 6 Unknown Facts? How is Hacking Conducted ?
How Do You Get Hacked ? 6 Unknown Facts? How is Hacking Conducted ?
follow on : https://www.instagram.com/?hl=en

We are living in a time , greatest of all time as we are surrounded with Technology , the Mobile Phones.
The Technology being evolved its easy to gain information about anything anywhere and anytime. As it is said " Information is Wealth " , there are few people who has the capability of using this information for or against anyone , anywhere , anytime . In short they have the ability of increasing or decreasing the value of anything they want to. With the Technology getting updated day by day it is also resulting in developing new fraud methods and scamming methods.
Internet being so big that its impossible to imagine is hence divided into 3 parts :
1) Surface Web - It is a part of World Wide Web which is easily accessible and searchable to anyone with standard web search engines .
2) Deep Web - Hidden part of World Wide Web which can't be easily accessible to anyone like confidential data or login id password . Example - Like we have our email id which can be accessed only by us with a particular id and password.
3) Dark Web - Part of World Wide Web which can't be easily accessible by normal browser , it can only be accessible with special browser .
VARIOUS METHODS OF HOW WE GET FRAUD / SCAMMED ?
1. Xerox facility : -

Nowadays no one uses the Xerox facility much since everyone owning a smartphone clicks the picture of essential documents or essential information directly which saves the cost of Xerox as well as saves their time , with the smartphone technology the xerox shops are unable to income much from Xerox Business so they involve in "Information Business " , where some Xerox shop sells the personal information of the customers to the clients ( buyers ) .
Example : If any customer comes for the xerox of his/her bank document or personal information , what some xerox shops do is they keeps an extra copy of the customers document . Now for that 1 data the xerox shops gets paid Rs 1 then for 50 data they get paid rs 50 , for 500 data copies they will get paid with rs 500 and with 50,000 data copies they will get paid with rs 50,000 . this count goes on , more the data some xerox shops provide to the clients more the money they get paid in return of this information. It is often possible that different types of data having its own different type of rates .
2 . Flight's Boarding Pass : -
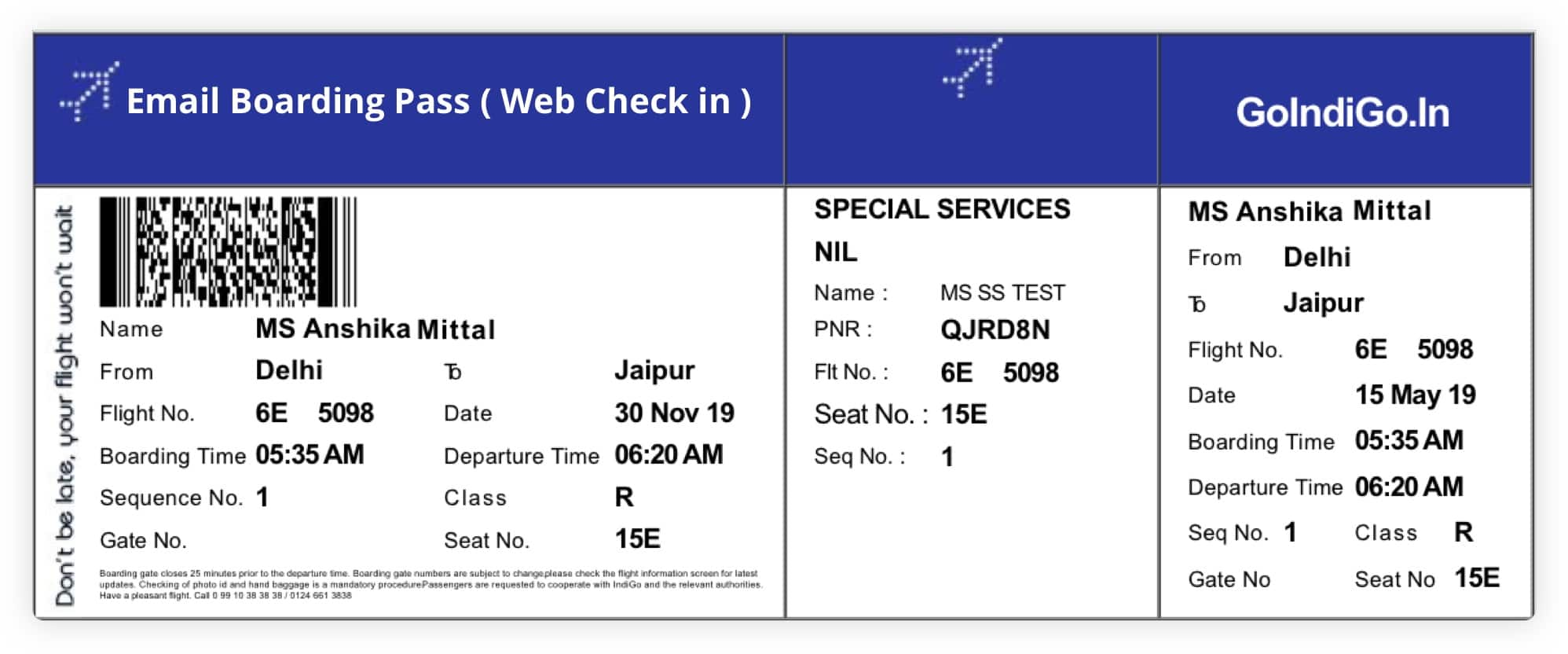
The Boarding Passes that we usually throw / dispose after our flight's journey has a QR CODE present in it , which if scanned then the fraudsters / scammers can gain access to entire life history of the passengers like his/her contact number , passport details and even bank details like from which credit / debit cards the flight ticket is being purchased . By selling these details one can earn a lot of money.
3 . Calls from Call Center / Finance Companies : -

We often get calls from Call Centers / Finance Companies regarding Credit Cards , Loan offers , Awards , Rewards , Foreign Trips , Lucky Draws Winner and many others . Ever wondered how do they get our numbers ? . The Call Centers / Finance Companies buys these information as they need new customers , new users every time , where as on the other hand the fraudsters / scammers also needs new users / customers every time as their new bait for fraud , so they buys these information from the Call Centers . Hence , this is the reason we get so many calls regarding several unwanted services and offers .
4 . Approval For Rejected Loans : -

There are many people who are in great need for loans for their various purposes but everyone doesn't get loan approval due to lack of meeting the loan approval eligibility criteria. Hence , when one bank rejects a loan applicant then other banks also doesn't easily approves the same loan applicant and a Reject list is created for those whose loans are being rejected . Now here's where the scammers / fraudsters finds an opportunity .
What they do is they make a contact with the rejected loan applicants via call / mail / meeting face to face claiming that they are the agents and can make the approval done for the rejected loans but they will charge some percentage from the approved loan amount as their commission , the loan applicant ( customer ) trusting the agent finds the deal attractive and submits all the original documents of his / her to the agent . Soon after the submission of documents within few days the loan is sanctioned and transferred to the account of the customer , the whole procedure will seem like its real so no one can doubt the agent but the twist in the story begins when after 2-3 days of the loan amount sanctioned in the account suddenly disappears and the loan being sanctioned in an illegal way with the help of unknown agent , no one can file a police complain and non one track the culprit ( fraudster ) . After all this what you get left with you is to fall under the repayment for the interest you need to pay to the bank for availing the loan ( which is now stolen ) .
5 . Unnecessary access to Mobile Apps

There are several Apps which we install and we permit it to access our location , phone number , messages , email account , gallery , microphone . Ever thought what's the use of permitting these unnecessary actions ? . With just permitting and installing unnecessary apps in our mobile the hacker can get access to every private to public information present in our mobile , which the hacker can mis use against he / she .
6 . Social Media / Online Adds ( Offers ) : -
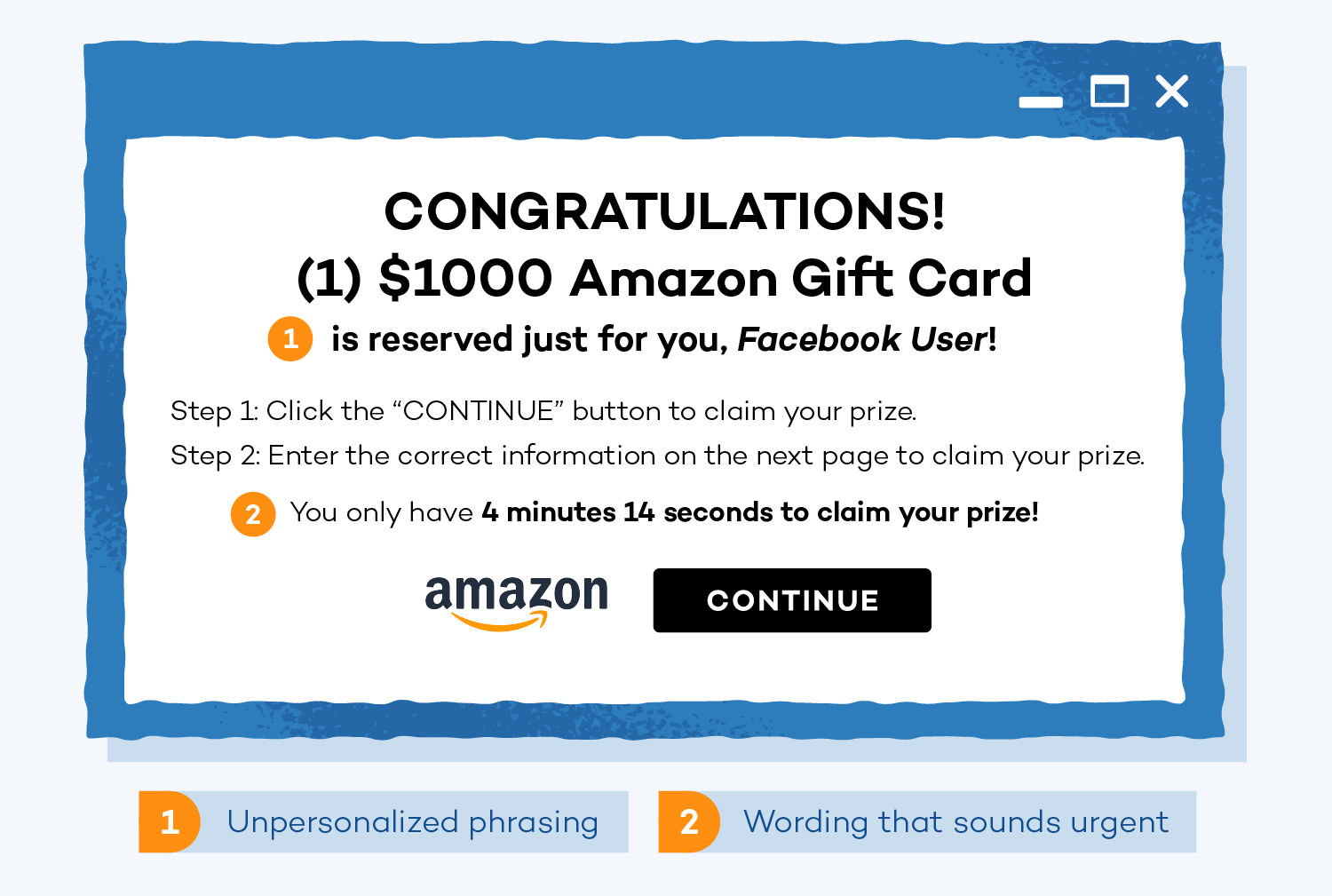
We visit several website while net surfing and we often find these adds offering awards , rewards cashback prizes , and many other offers enough to bait a person , now when the person clicks the add the chances increases that his / her mobile gets hacked with just one simple click , sometimes the option comes for filling out the necessary details about us like email id , address , contact number and by filling these information in these unknown source the hacker gets all the necessary information enough to hack you down withing seconds .
We even receive some unknown links via messages and the moment we click on it any malicious app starts downloading and installing which can be harmful for your device . This is known as the"Phishing Attack" .
How are these scams / frauds conducted ?
These scams and fraud cannot be conducted by the Internet so they are conducted through DARK NET (A network of secret websites , which isn't visible to search engines ) . Dark Net can only be operated with a browser named as "Tor ", an Onion Ring . Every illegal job is done with the help of Dark Net like : - Black Marketing , Weapon Dealing , Drugs , Currency Exchange , Child Trafficking , Terrorism, Film Piracy and every other illegal work present in the Globe is conducted via Dark Net .
Why was Dark Net created ?
Dark Net was coined in 1970's to designate networks isolated from ARPANET (government founded military network which evolved into the internet )
Why is the Browser named as "Tor " ?

In 2002 , the Naval Research Laboratory of the US Navy developed a software to update their security system so that their communication cant be accessible by anyone else , so they names the browser as "The Onion Router " which is known as the "Tor Software " in short . It was named so as every lines and layer present in onions is curved so also when the data will be transferred from one end to other it wont go directly , it will re route from global connections present worldwide , which makes the user untraceable.
Highly informative piece of information you've written. Great job.
ReplyDeleteThanks for good information
ReplyDeleteAwesome article. Good luck for you.
ReplyDeletecheck out our latest post ...
How to verify your domain on facebook
How to unblock website from facebook & instagram
How to download windows 10 pro latest version iso file
Top 10 blogger tips and tricks । Blogger tutorial
mrlaboratory.com : All kind of internet technology tricks are share on our website.. 47